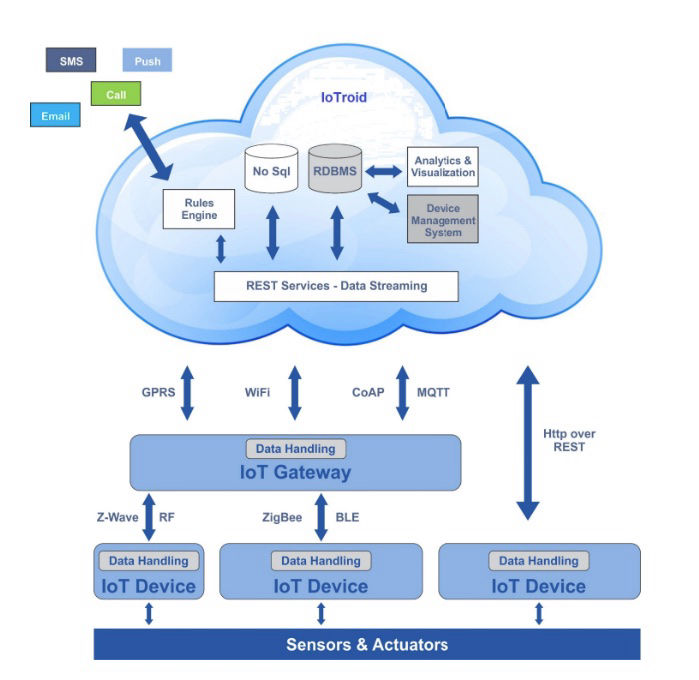
IoTroid is an award winning IoT middleware that makes it possible to create tailor made applications which are easy to use and fast in performance.
Design products and define new features based on information about how customers are using the products.
Loggers and sensors can be connected quickly and easily without having to worry about any protocols.
Filtered, aggregated and processed data is sent as final responses, for storage or for further in-depth analysis.
Seamless data integration with information in other systems and platforms within or outside the organization.
Know before a problem arises and when products are on or offline so that issues can be resolved quickly,
Add new products, services and capabilities to solve customer problems and meet customer demands.


Sensors
Various types of sensors collect a wide variety of information and generate output as signals. The information is sent through communication protocols. The nodes forward the data to the gateway.
Gateway
Gateways connect to the IoT devices, communicate via specific protocols, store and parse the information and then send them over to IoTroid for processing and analytics. They not only abstract the medium of communication but also provide the secure channel required for the transmission of this data.

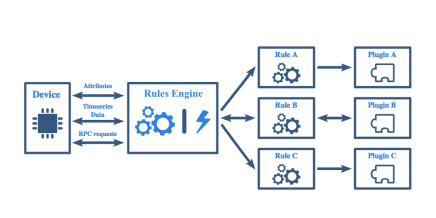
Rules Engine
IoT Rules are loaded into the IoT Rules Table, which is stored in the non-volatile memory. This table is simply a list of supported sensors, sensor data types, minimum and maximum values and routine reporting intervals. The real-time Rules Engine transform messages based on predefined expressions.
Smart Devices
The data collected from sensor nodes is transmitted to the IoTroid Engine. It is then stored and processed securely. The processed data is then used to perform intelligent actions that make all our devices
"Smart Devices"!

IoTroid cluster scales horizontally and linearly. There is no single point
of failure in IoTroid cluster architecture.
No single point of failure. Geographical redundancy. The endpoint data is stored in fault-tolerant databases.
Communication protected by
the latest security practices. Proactively seeking out and eliminating vulnerabilities.